Altosec, performs mitigation before traffic reaches your web server.
Starts working immediately when you change the A record on your DNS server with Altosec IP address.
All traffic is routed to the NG-WAF, filtered and sent directly to your original servers.
7/24 uninterrupted service with redundant NG-WAF service running in different data centers.
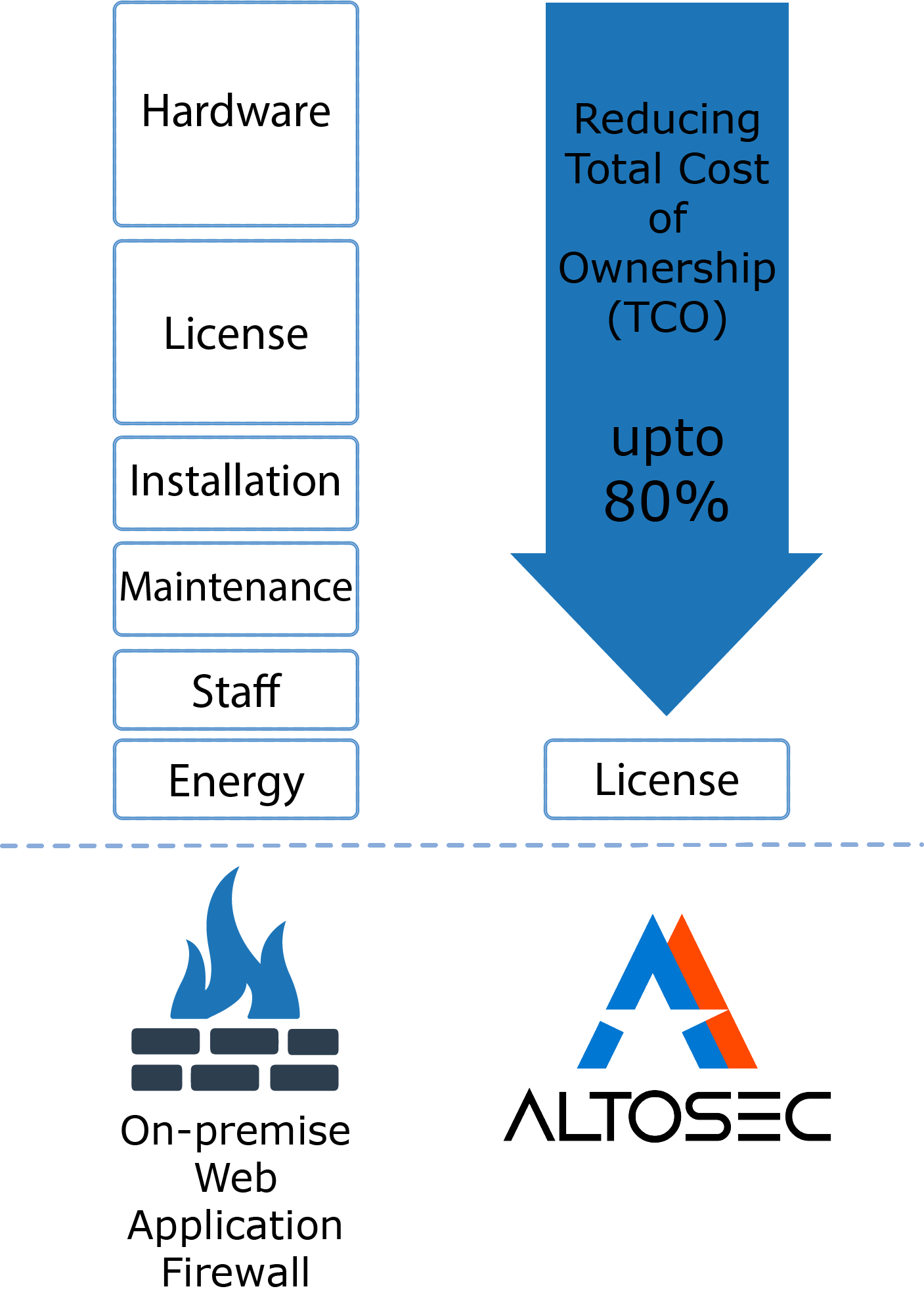
On-premise WAFs need to be updated regularly to protect against new threats. You do not need to make any software or hardware changes with Altosec NG-WAF.
You do not have to employ security specialist at your organization.
You can pay as you need with the scalable infrastructure.
ARTIFICIAL INTELLIGENCE
Altosec’s AI solution automatically detects and responds to even unknown attacks in real time without any human intervention.
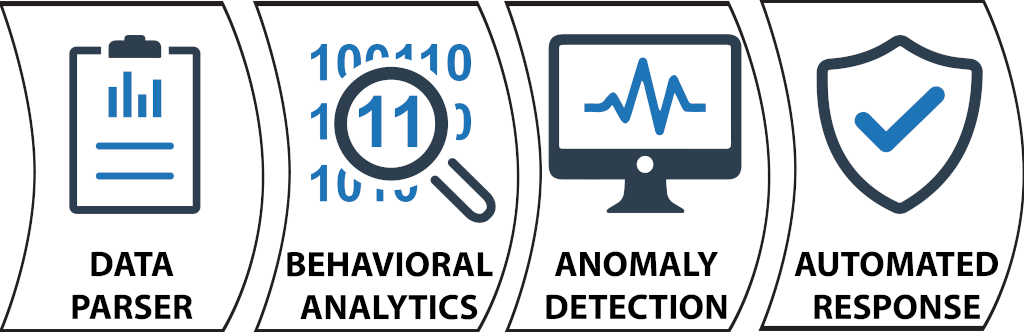
Collect and parse rich network metadata, relevant logs and events in real-time
Identify attacker behavior with artificial intelligence
Robust anomaly detection capabilities after a deeper inspection
"No operator" solution that protects the network automatically
FREE SSL CERTIFICATE
Setting up HTTPS for your site typically starts with a purchasing an SSL certificate. Then, you have to upload the certificate file to your web server and repeat the process for renewal regularly. Also, you’re required to manually change all website links to HTTPS.
Altosec’s free SSL service utilizes Let’s Encrypt certificates issued individually to cover each of your domains. If you already have an SSL certificate, you can use your own as well. All these processes like certificate installation and renewal are automated for our users.
SSL Offload prevents the web server from attempting to encrypt and / or decrypt the traffic, so page load speed increases with better web server performance.
Load balancers can inspect the HTTP traffic (i.e. sticky session) and improve user experience and optimize network resource usage.
SSL Bridging involves decrypting the traffic on the Load Balancer, inspecting the HTML code and filtering it for malware and any content policies that may be applied. The traffic is then re-encrypted usually using a different certificate.



